by Ben | Jun 24, 2016
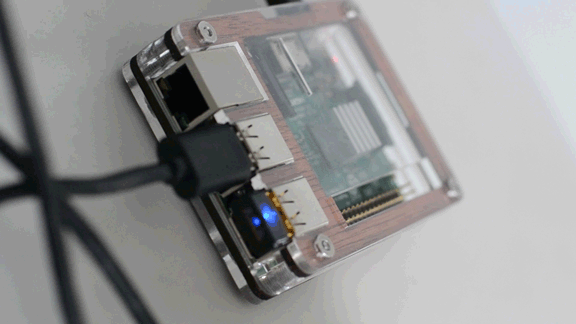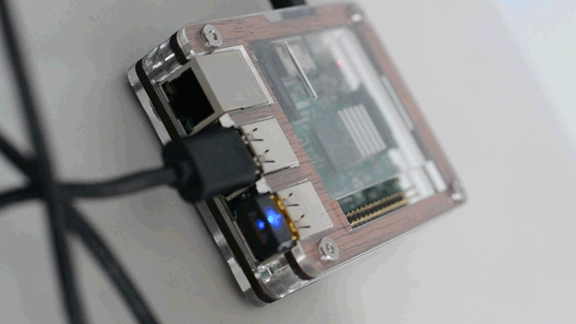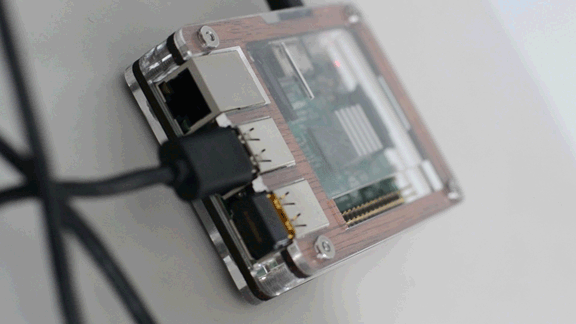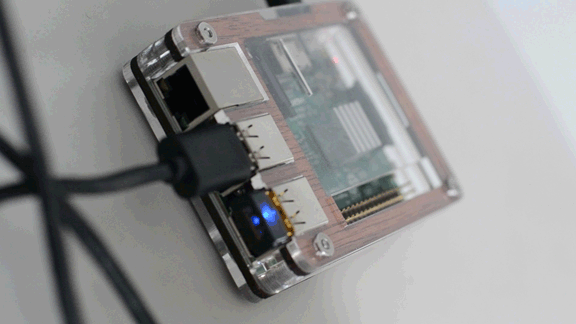
I needed to compile drivers for the Raspberry Pi Edimax AC450 EW-7711ULC Nano USB WiFi Adapter that I picked up for less than $20 at Amazon to bring 5GHz connectivity to both my RPi2 & RPi3B. OF COURSE I check the officially supported devices list after I bought...

by Ben | Apr 23, 2014
You might be wondering – how has the Raspberry Pi NAS held up after 1 year, 9 months, and 29 days of traveling & heavy usage daily? Surprisingly well actually. Roll up the sleeves and read on. *** UPDATED 4/9/2016 *** rewrote lsyncd config for version...
by Ben | Jan 25, 2009
If you’ve ever been responsible for maintaining an Apache web server, you know how important security is. Nikto provides an easy way to scan for known (and unknown) vulnerabilities within your Apache server. Actually, it does a fairly comprehensive scan on...
by Ben | Jan 25, 2009
The easiest way to get a CPU temperature readout from Linux is by looking at an ACPI function called temperature: [code] cat /proc/acpi/thermal_zone/THRM/temperature [/code] You could also try sensors-detect and then sensors, but I had some trouble detecting the...
by Ben | Jun 25, 2008
When it comes to typography, Microsoft TrueType fonts are both visually appealing and aesthetically pleasing. They’re found all over the web, usually specified in stylesheets. Unfortunately for Linux users, the most common TTFs aren’t installed (by...




