When configuring the networks of a virtualized environment, private VLANs expand the functionality of a standard VLAN. This article describes the configuration of PVLANs from both the VMware and Cisco perspectives. The purpose of this article is to provide a brief configuration overview. It’s likely you already know what PVLANs are and how they work, so I won’t go into much detail there. For more information about VLANs and PVLANs, check out Cisco’s Securing Networks with Private VLANs and VLAN Access Control Lists.
Usage Scenarios
- DMZ security – Servers running in a DMZ can be isolated from one another. Should a DMZ guest be compromised, the guest is unable to communicate with any other guest in the the DMZ (given each are a part of an isolated PVLAN)
- Hosted cloud infrastructure – A customer environment (consisting of multiple guests) in a community PVLAN are able to communicate amongst themselves, but cannot communicate with a different community PVLAN
- Overcome standard VLAN limitations – While PVLANs exist with their own set of limitations, private VLANs greatly extend the functionality and usefulness of a standard VLAN
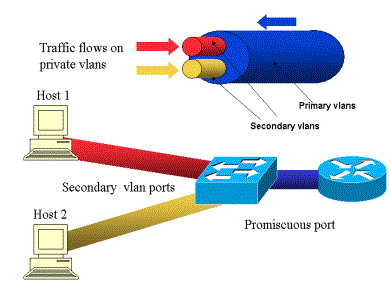
Configuration Overview
vlan 2410 int: 192.168.7.1 (primary 2410, secondary 2411)
vlan 2412 int: 192.168.8.1 (primary 2412, secondary 2413)
vlan 2411 – isolated
vlan 2413 – community
bperove-vm1: 192.168.7.10 – dvPortGroup1 – primary 2410, secondary 2411
bperove-vm2: 192.168.7.11 – dvPortGroup1 – primary 2410, secondary 2411
bperove-vm3: 192.168.8.10 – dvPortGroup2 – primary 2412, secondary 2413
bperove-vm4: 192.168.8.11 – dvPortGroup2 – primary 2412, secondary 2413
bperove-vm5: 192.168.8.12 – dvPortGroup2 – primary 2412, secondary 2413
bperove-vm6: 192.168.8.13 – dvPortGroup3 – primary 2412, secondary 2412
Configuration of VMware vDS (DVS)
dvSwitch Settings
dvPortGroup Settings
VLAN Configuration
|
1 2 3 4 5 6 7 8 9 10 |
vlan 2410 private-vlan primary private-vlan association 2411 vlan 2411 private-vlan isolated vlan 2412 private-vlan primary private-vlan association 2413 vlan 2413 private-vlan community |
Interface Configuration
|
1 2 3 4 5 6 7 8 9 |
interface Ethernet1/19 description bperove - bs-tse-i127 - vmnic2 switchport mode trunk switchport trunk allowed vlan 2410-2411 interface Ethernet1/20 description bperove - bs-tse-i127 - vmnic3 switchport mode trunk switchport trunk allowed vlan 2412-2413 |
Communication logic
vm1 can ping vlan 2410 int @ 192.168.7.1, but cannot ping vm2
vm2 can ping vlan 2410 int @ 192.168.7.1, but cannot ping vm1
vm3-5 can ping vlan 2412 int @ 192.168.8.1, and can all ping each other
vm6 can ping vlan 2412 int @ 192.168.8.1, vm3-5, and vm3-5 can ping vm6
vm1-2 cannot ping vm3-6
Obligatory clip from Silicon Valley


There are 5 comments