by Ben | Oct 31, 2010
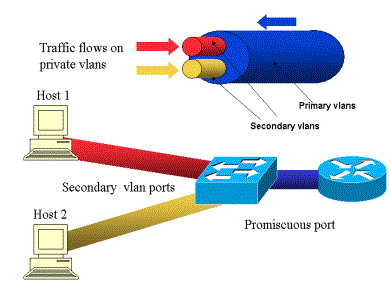
When configuring the networks of a virtualized environment, private VLANs expand the functionality of a standard VLAN. This article describes the configuration of PVLANs from both the VMware and Cisco perspectives. The purpose of this article is to provide a brief...

by Ben | Sep 16, 2009
What’s it like to install a wireless network in a casino?  With the help of two others, we lit up ~200 APs at the Ameristar in Black Hawk just a few weeks before the grand opening on 9/29. This was a ton of work, but it was worth it. Here are some photos...




