
by Ben | Nov 8, 2017
Recently I got this awesome phone, but I wanted to add one last finishing touch of customization to my shiny new device: install custom system fonts on the Google Pixel 2 XL. Most font changers can only install fonts properly with a rooted device, but none of them...
by Ben | Jun 24, 2016
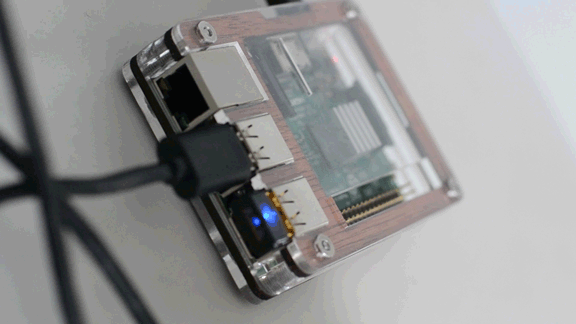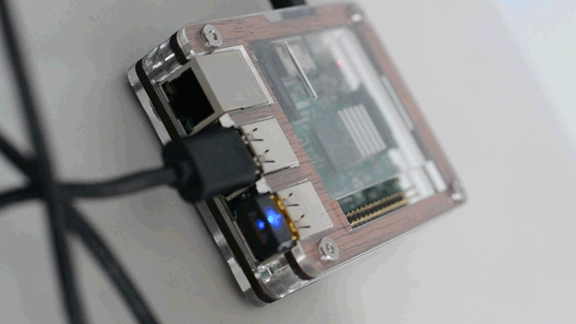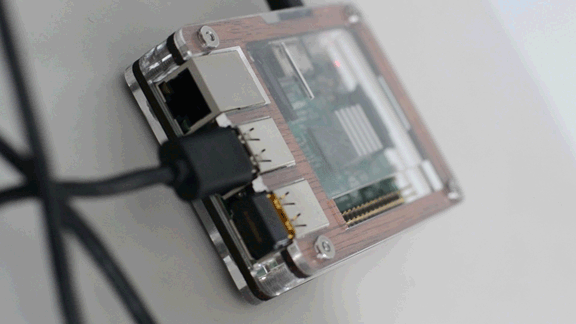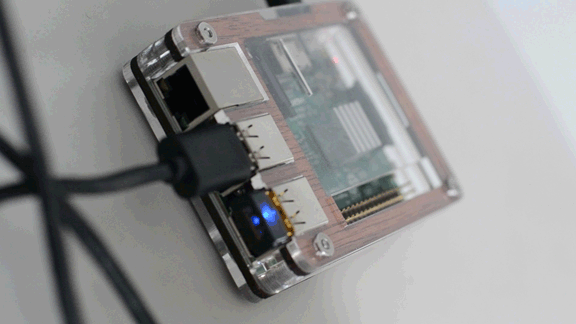
I needed to compile drivers for the Raspberry Pi Edimax AC450 EW-7711ULC Nano USB WiFi Adapter that I picked up for less than $20 at Amazon to bring 5GHz connectivity to both my RPi2 & RPi3B. OF COURSE I check the officially supported devices list after I bought...

by Ben | Mar 15, 2016
Over the years, you could say that I’ve gone through a couple phones. I’ve had to copy & restore data from the old phone to the new phone numerous times. As a result, my photos have become wildly disorganized. Photo dates no longer match the actual...

by Ben | Apr 23, 2014
You might be wondering – how has the Raspberry Pi NAS held up after 1 year, 9 months, and 29 days of traveling & heavy usage daily? Surprisingly well actually. Roll up the sleeves and read on. *** UPDATED 4/9/2016 *** rewrote lsyncd config for version...
by Ben | Aug 9, 2012
My apologies to Tommy – this post was somehow lost. Please be patient as I go through the backups… Found the backup. Need to restore it better. ‘\r\n\r\nHaving spent less than $500 on lenses for my Nikon D3100 with no prior experience, I\’ll...
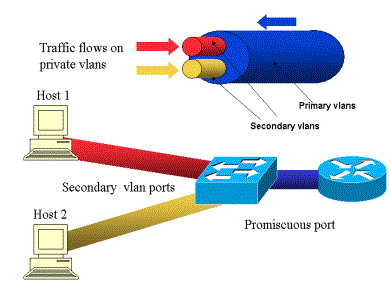
by Ben | Oct 31, 2010
When configuring the networks of a virtualized environment, private VLANs expand the functionality of a standard VLAN. This article describes the configuration of PVLANs from both the VMware and Cisco perspectives. The purpose of this article is to provide a brief...




